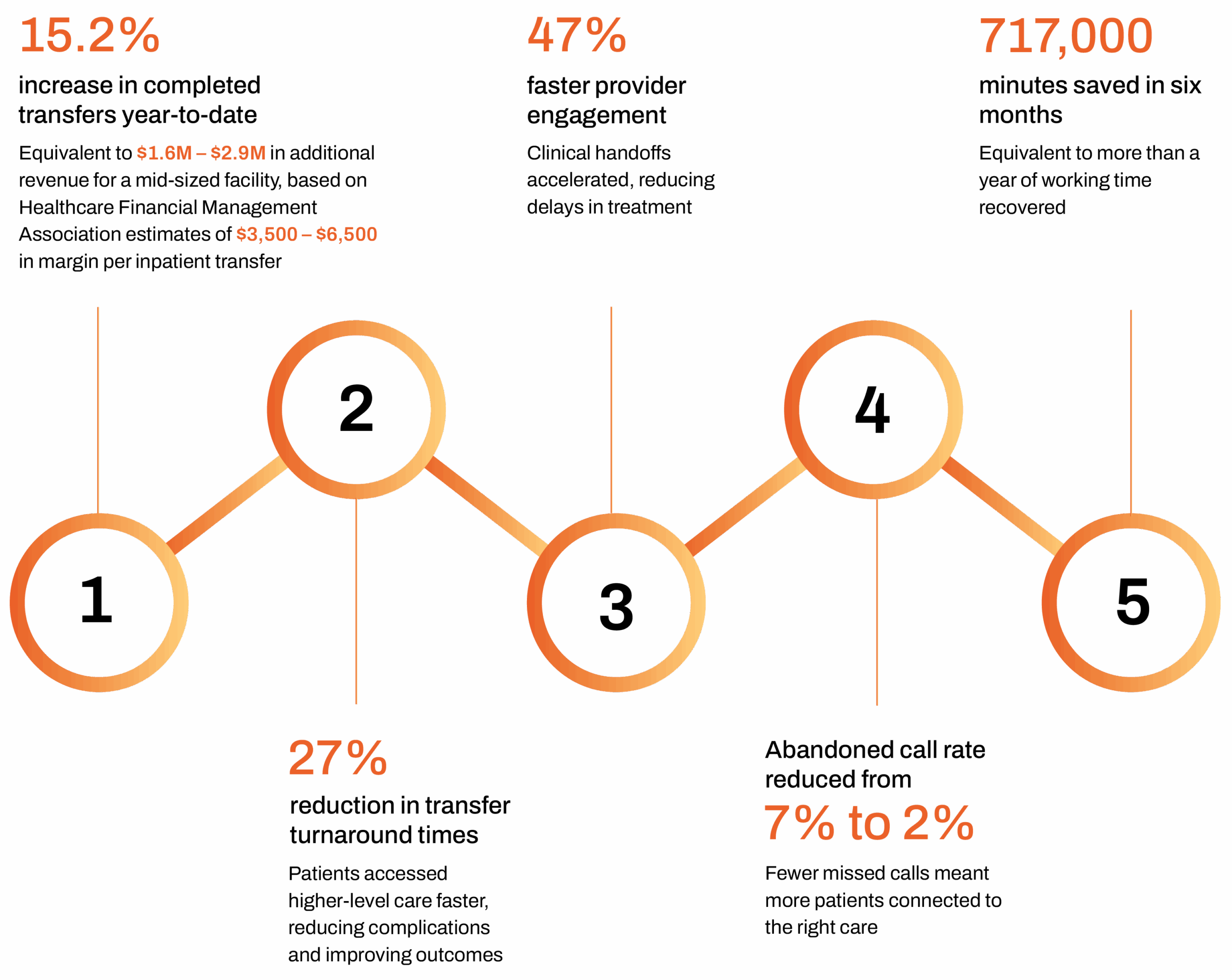
URL filtering used to be a static gatekeeper, blocking “malicious” websites based on outdated lists. But in 2025, threats have evolved and most filtering solutions have not kept up.
Today’s phishing attacks are AI-powered, highly targeted, and built to bypass legacy URL filtering systems. At Lockstep Technology Group, we help organizations move beyond reactive filtering by implementing Palo Alto Networks’ Advanced URL Filtering within your broader security strategy.
The Threat Landscape Has Changed
Phishing continues to dominate the threat landscape, both in volume and in impact. According to recent industry data:
- 84% of organizations experienced successful phishing attacks in 2022.
- 91% of security incidents were phishing-related.
- AI tools like FraudGPT and PoisonGPT are being used to scale and personalize attacks.
Traditional URL filtering struggles to keep up because:
- Phishing sites are often used only once.
- Attackers rapidly create and abandon new domains.
- Static crawlers fail to access gated content or mimic real user behavior.
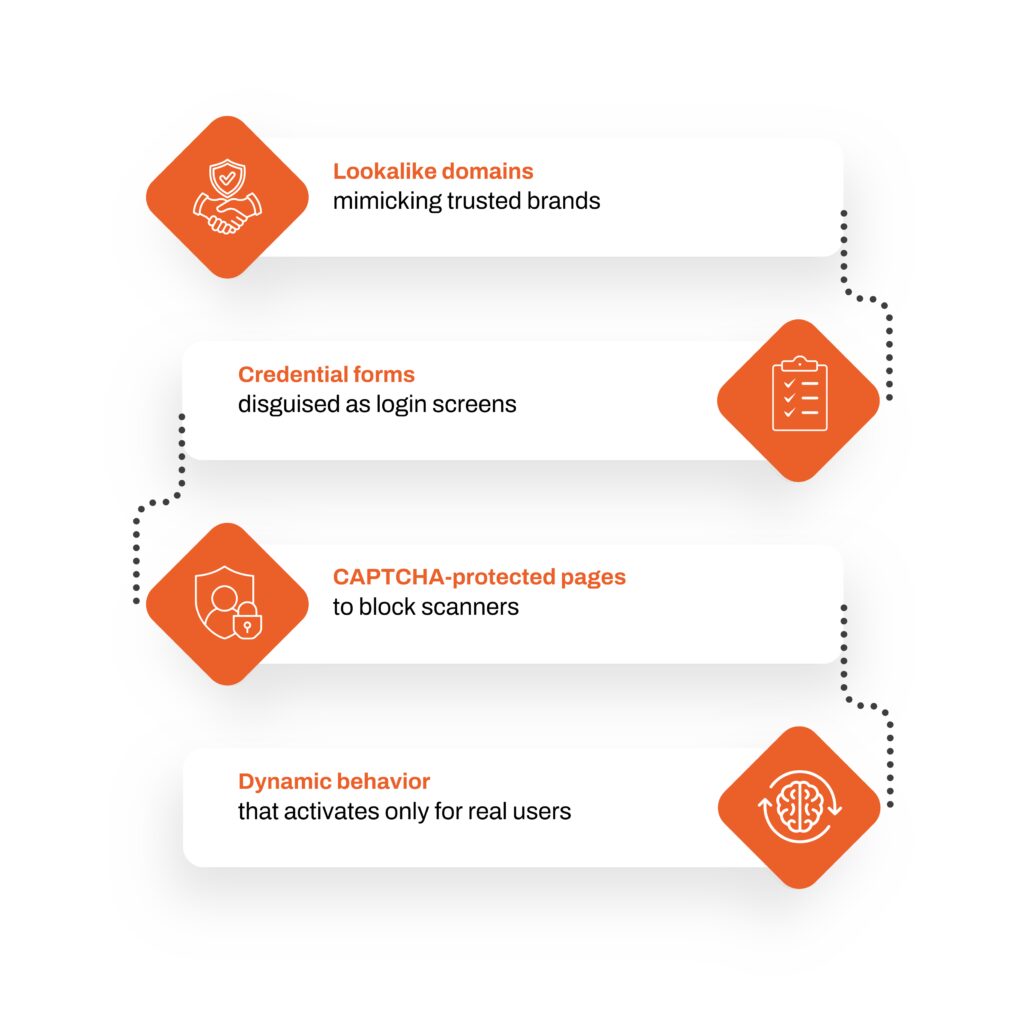
Tactics Used in Modern Phishing Pages
- Lookalike domains mimicking trusted brands
- Credential forms disguised as login screens
- CAPTCHA-protected pages to block scanners
- Dynamic behavior that activates only for real users
Understanding Real-Time URL Filtering
The webinar included a live demo where Palo Alto Networks showed how their solution analyzes inline traffic in real time as users interact with web content.
This goes far beyond category-based blocking. Their engine evaluates:
- Page behavior (e.g., login forms, CAPTCHA bypass)
- URL history and domain age
- Dynamic content behavior
- User interaction flow
This means phishing sites that evade traditional detection are blocked instantly even if they are brand new.
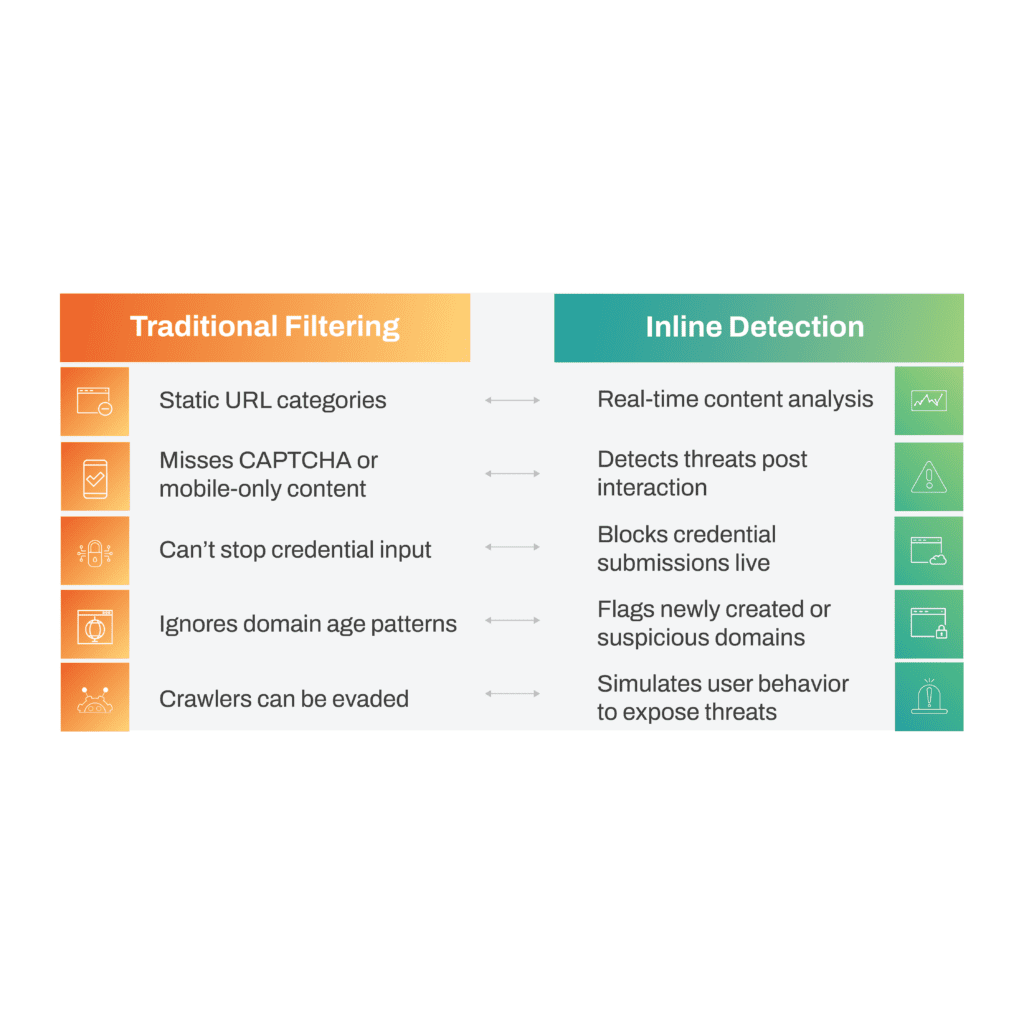
Inline Detection vs. Traditional URL Filtering
| Traditional Filtering | Inline Detection |
| Static URL categories | Real-time content analysis |
| Misses CAPTCHA or mobile-only content | Detects threats post interaction |
| Can’t stop credential input | Blocks credential submissions live |
| Ignores domain age patterns | Flags newly created or suspicious domains |
| Crawlers can be evaded | Simulates user behavior to expose threats |
Why Implementation Matters
While Palo Alto provides the engine, implementation is where the impact happens. That is where Lockstep comes in.
We help you translate Palo Alto’s advanced capabilities into a secure, usable, and policy-aligned deployment. By tailoring filtering policies and user experiences, we enable you to:
- Customize filters by user group or role
- Implement credential protection without disrupting access
- Analyze real-time logs to support threat hunting and policy refinement
- Avoid unnecessary friction for your users
The Shift from Filtering to Prevention
The webinar highlighted a critical point: Phishing is no longer just an email problem. Today, malicious links are delivered through SMS, chat apps, and even shared documents.
With Advanced URL Filtering, organizations can detect and stop these threats before users interact with them, but only if the system is deployed and governed effectively.
Lockstep’s role is to bridge the gap between cutting-edge capability and operational reality. We help organizations in K-12, higher ed, and enterprise environments move from passive filtering to active prevention without overwhelming your IT team or breaking trust with your users.
Ready to Rethink Web Protection?
If you are still relying on outdated URL filtering systems, it’s time to reassess.
Talk to Lockstep about implementing Palo Alto Networks’ AI-powered solution to protect your users, data and reputation.