Secure Your IT
Environment with
Managed Cybersecurity
Services
Facing the New Cyber Reality

Targeted attacks on sensitive data, including student records and patient information

Vulnerable and unmonitored devices across distributed and remote environments

Overstretched IT teams with limited staff and budgets

Increasing regulatory and compliance requirements, including FERPA, HIPAA, and CJIS

Effective cybersecurity starts with asking the right questions
Most cybersecurity programs fail not from a lack of tools, but from deploying them without fully understanding the environment they protect. Lockstep Technology Group starts every engagement with a comprehensive assessment to identify real vulnerabilities, validate existing controls, and pinpoint where internal resources are strained. This ensures that every security decision is based on evidence, not assumptions.

Supported by Trusted Technology Partners










Tailored Cybersecurity Services for Complex IT Challenges

Security Advisory & Assessments
Identify critical vulnerabilities, prioritize remediation, support compliance, and guide Zero Trust strategies with risk-based assessments.

Network & Perimeter Security
Deploy firewalls, content filtering, and email security to protect distributed environments and ensure secure access.

Endpoint & Device Security
Use EDR, antivirus, and mobile device management to secure all endpoints, including remote and unmanaged devices.

Identity, Access & Zero Trust
Enforce Zero Trust with access controls, multi-factor authentication (MFA), and identity governance that reduce lateral movement.

Security Monitoring & Detection
Enable 24/7 monitoring with real-time alerts, event correlation, and visibility for faster threat response.

Vulnerability & Asset Management
Continuously scan for risks, close security gaps, and stay audit-ready with real-time asset intelligence.

Outcomes You Can Count On

Reduce downtime during cyber incidents
Limit disruption to classrooms, clinics, and public services with resilient infrastructure and faster containment.

Alleviate pressure on internal IT teams
Offload day-to-day security tasks through expert support that extends your team’s capacity.

Simplify compliance and audit readiness
Maintain alignment with FERPA, HIPAA, CJIS, and NIST through clear documentation and well-defined controls.

Strengthen security over time
Continuously adapt to new risks, technologies, and operational needs with long-term guidance from Lockstep.
Featured Resources
Foundational Security Assessment
A comprehensive assessment of your environment, focused on identifying the vulnerabilities threat actors target most.

Detailed Project Plan
A prioritized roadmap to improve your security posture

Executive Overview
A high-level summary for leadership decision-making

CIS Benchmark Score Sheets
Clear measurement against industry best practices

Ransomware Risk Analysis
A quantified snapshot of your current exposure level
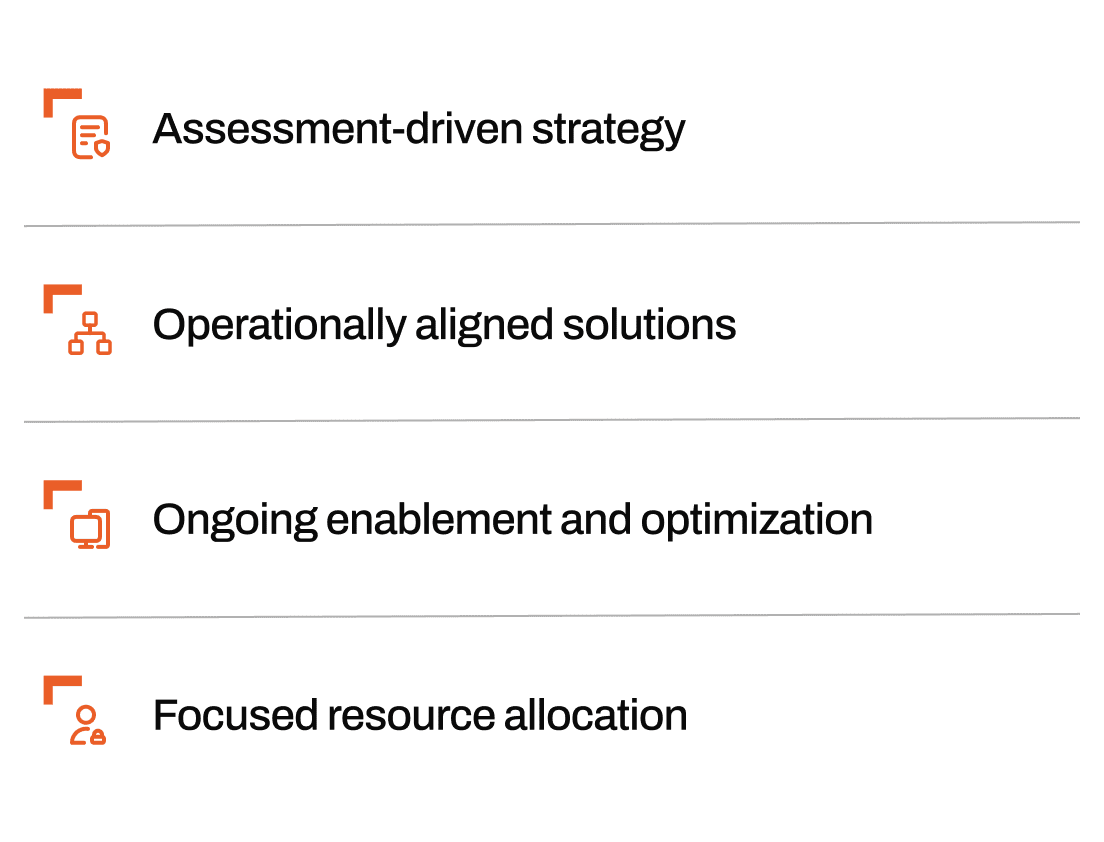
A Complete Strategy for Long-Term IT Security

Connect
We design resilient IT environments by aligning infrastructure, access, and operations to reduce risk and simplify complexity from the start.

Empower
We help you adapt to new threats with ongoing optimization, performance improvements, and compliance support without adding strain to your team.